
There is a rogue form of IT that lurks in the shadows of big organizations. Shadow IT crept into the frustrating information system of companies to make it less troublesome for the employees.
It operates in the dark to further the employees’ effectiveness in their roles by giving teams the tools they need outside of centralized IT for them to do their jobs as best as possible.
There’s a story behind how this rogue IT came about, how it has magnified over time, and how despite its drawbacks, it has many upsides as well.
Digging a little deeper in understanding what is Shadow IT?
A well-known definition describes Shadow IT as the use of technology, software, applications, devices, etc., outside the formal control or governance of the CIO and the IT department. Shadow IT has grown immensely over the past few years. One main reason behind this is the growth and adoption of SaaS-based software and applications. While one school of thought is that Shadow IT drives innovation and productivity, the other is it puts the security of information and data at risk.
A vast majority of IT decision-makers, around 95%, acknowledge the potential risks associated with Shadow IT. These risks may include a lack of proper data governance, unclear ownership, and inadequate change control mechanisms.
Continue reading this blog to see how a lurker in the shadows is also a friendly neighbourhood helper.
The origin
Chapter 1: The advent
There was once a time, many years ago, when a company’s employees were highly dependent on their IT department. The technology that was disseminated to the users is what they accepted as theirs.
It essentially worked as: innovation in the market + IT department = technology for the enterprise.
innovation in the market + IT department = technology for the enterprise
For example, typically a company worked like this:
- The IT professionals i.e. the IT department of the company would work on the configuration settings and governing the technological infrastructure to secure the data of the clients and the company. This was their job.
- Departments would give their feedback about technology but the gatekeeping job was reserved for the IT department.
In the meantime, a new trend was being set in the market. As the 2000s arrived, the internet was massively adopted as the new norm, new technology came into the market that allowed the outside and the inside to merge.
Along with this, the users were becoming more and more tech-savvy with each passing day and this is what marked the advent of Shadow IT.
Chapter 2: Taking over the reins
This liberty to handle challenges on their own without dependency on the relatively slower IT processes made the employees feel empowered enough to take matters into their own hands.
Basically, they used the internet. And easily accessible external hardware, such as flash drives.
In the midst of this independent working, the employees failed to mention the nitty-gritties to the IT department; and did not fathom the fact that their unsupervised actions came with consequences. You can also check out Citizen Developer’s Toolbox: Insights and Strategies from Our eBook-Innovate and Empower: A Journey through Citizen Development!
Chapter 3: New reality
This innovation was given the tag of “Shadow IT.”
Shadows hide the composition of things making them visible but at the same time, unseen. These lurking shadows threatened the company’s IT because they were being kept in the dark. They simply did not know what was going on in aspects that were related to their department.
To the employees, these cloud services were very useful. It helped avoiding time-consuming tasks, increased reactivity, and hence, productivity.
Approximately 79% of IT professionals are of the opinion that utilizing Shadow IT endangers company data. This is because these platforms are not rigorously vetted to ensure that they can effectively safeguard sensitive business and customer data.
To the IT department, however, they looked at it as a threat to data security and an undoing of their hard work to secure the tech of the company. This was simply because the softwares and devices that were able to access the data of the company was unknown.
Moreover, how was IT supposed to figure out which ones were leaking the company’s system to outsiders? How were they supposed to deal with the viruses entering the company’s systems from the employees’ external hardware?
The new reality was that the employees solutions were creating problems for IT.

The acceptance of Shadow IT
Now, with most people being extremely tech-savvy; Shadow IT has not only increased but has also been accepted. It is looked at as an innovative force rather than a troublemaker.
It has helped employees with boosting their productivity and performing well for their personal and professional growth and the development of the company as a whole as well. It is all very meta and cannot be looked at as a threat anymore.
The business environment today is extremely competitive and dynamic. Older processes are too slow for employees to do their best.
Also, it is but obvious that the people interacting with the market directly will have a good understanding of what technology is good and what just doesn’t cut it. Business experience can sometimes trump over technological knowledge in understanding innovation culture.
Drawbacks
Now that you have a rough idea of how Shadow IT is beneficial, it is important to know the drawbacks of it so as to minimize its ill effects on the company i.e. manage it in the best possible way.
In a survey conducted by HP Wolf Security, it was found that 91% of the participants reported feeling compelled by their colleagues to sacrifice cybersecurity practices in the interest of streamlining business operations.
- IT isn’t able to do their job i.e. supply technology to the company since employees are finding solutions to achieve results themselves.
- There is a risk to security because while IT can see Shadow IT operate, it cannot connect the dots of what is going on within it. It is too contrasting to make sense of in a clear manner.
- It threatens the safety of data in a company. This threat is posed by hackers and also involves the threat of data turning redundant in a company. Basically, data silos is furthered with Shadow IT.
- Shadow IT contributes to the reduction of cost transparency for IT operations.
How are these drawbacks a problem for the company exactly?

1. IT cannot prepare for threats that they do not know
The job of IT is essentially to govern the technology and data of the company. If they do not know what is going on within Shadow IT, they are not in control. As a result, risks increase.
2. Risky business, quite literally
The more applications and softwares in the company, the more risk. How can IT monitor and protect every single application provider that is brought in?
Securing the infrastructure is insufficient to ensure every vulnerability gap is closed. There will simply be too many hidden openings into the company’s system.
3. Too many business determinants are uncontrolled
There is a risk of operations, dependency on vendors, market fluctuations, crowds, and saturations. It is too difficult to manage technology when so much time and effort is used for something that may or may not even last for a long span of time.
4. Data sharing is a task in itself
With more and more applications in the company, there are more places for data to exist. This information everywhere is difficult to keep track of.
What cannot be assimilated together makes it difficult to leverage the best use of it. The meaningfulness and utility of the information are harder to decipher and utilize.
5. It hampers common digital space sharing
Imagine this. One department in the organization is on Skype, another on Google Hangouts, and another on Zoom. All three departments have tasks spread across them.
People are talking but there is no commonplace (which mind you, is a bare minimum requirement) where collaboration can be facilitated. As a result, a collaboration between teams is hampered in the organization.
6. Birds eye view is lost
By focusing on so many different aspects, too many details create confusion and lots of time to sort that out. There is a need to objectively measure the technology’s usefulness in the company.
If three departments have used three different platforms for their solutions to the same problem in context to their work, wouldn’t it be extremely tough to assimilate everything into one report to overview it entirely?
7. There are much bigger fish to fry
Shadow IT is a small part of a much larger concern. Employees know that these tools can be risky, they use it anyway because ultimately, it does aid in their productivity and is honestly just really convenient for their work processes.
The organization’s goals are supposed to be achieved in the end. There’s a bigger picture aspect to it.
Would you just smile and pay for a few licenses to solve an issue or ask a backlogged IT team to create a customized solution with a large amount of data with very many intricacies?
How to capitalize on the benefits and minimize the drawbacks of Shadow IT?
- Well for one, you can spread IT across business units.
- Create and communicate borders that are clearly defined when it comes to cloud applications.
- Try to reduce the shadow aspect of shadow IT as much as possible i.e. make visible what is not.
But since Shadow IT exists because there is a demand for new technology that keeps up with the fickle and dynamically changing market; and because rigid technologies are highly unappreciated by employees who look for task-specific customizable tools to aid their workflows, another solution is considering the use of no-code platforms.
Also read: Myths About Low-Code No-Code Platforms Debunked
How do the risky blurry boundaries of Shadow IT help the emergence of Business Led IT?
Shadow IT, while having its drawbacks, is believed to be helping businesses in increasing productivity and driving innovation. It was important for business leaders to take notice of this silver lining while trying to destroy the so-called Shadow IT culture. That is where the concept of Business Led IT comes into the picture. Although business-led IT is also outside the control of the CIO and the IT department, it is different because it is aligned with the business units and their needs.
Business-led IT is a deliberate method of distributing I&T efforts and accountability across an organization that is backed by a service-optimized IT operating model and IT governance, at the very least. This helps businesses reduce the risks associated with Shadow IT, such as data security risks, integration issues, ambiguity, and inefficiency in work. Business-led IT lessons the IT department’s burden of creating a new solution and freeing up their time solving critical business issues.
Using No-Code to deal with Shadow IT
No-Code platforms are application builders that have simple visual interfaces to aid a user to integrate it with other programs in whatever way they desire. It is customizable and enables solution development much quicker than any other means.
Applications are made by citizen developers to aid the company’s work processes. This builds the speed, agility as well as security of the enterprise.
IT backlog is the reason that employees look elsewhere for help. It is not possible for IT to meet every single need and demand of the employees in the business, it’s just not feasible.
Shadow IT around no-code is avoided as it allows developers to economically and quickly create applications. There is no more waiting for development.
There is so much flexibility and immediacy with which changes can be made that the Shadow IT dependency decreases significantly.
Also read: How to Implement and Govern Citizen Development in Your Organization
Here are 5 steps for no-code to tackle Shadow IT:
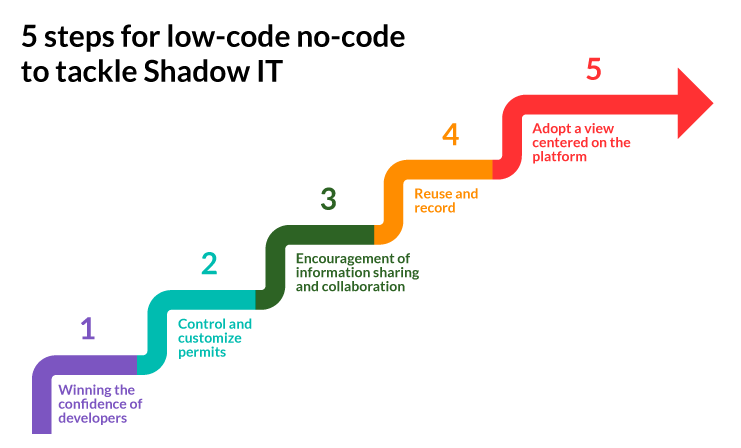
- Winning the confidence of developers: Integration is much more important than the interface; this should be focused on as well as opening backends. This gains the respect of developers.
- Control and customize permits: Policies for access control should be established with fine-grained permits. Application privileges, data models, and users should be governed by IT.
- Encouragement of information sharing and collaboration: Workflows can be automated with no-code so as to enable collaboration and develop a simple route to production from mock-up.
- Reuse and record: Anything undocumented is unmanageable. Departments should be encouraged to document and show reusable resources to processes.
- Adopt a view centered on the platform: No-code becomes the standard means of solution for problems that may arise. Therefore, standardization and adoption of a no-code community on a single platform creates a very helpful culture in the organization.
Conclusion
The business has come a long way in all these years. Shadow IT cannot be removed from the picture but can definitely be managed well by employing no-code platforms in the businesses and gaining some sort of control over processes.
Quixy is a no-code platform that can aid in making shadow IT inconvenient. Its drag and drop system enables the custom building of applications as well as the safety and security of data, all in one place for the company’s employees.
Get started with our platform, and experience the ease of automated processes and personalized app building.
Frequently Asked Questions
Here are some frequently asked questions about Shadow IT and Citizen Development. These answers will help you understand the concept of Shadow IT and how Citizen Development can mitigate the risks associated with it.
Q. What is Shadow IT & why is it a concern for businesses?
Shadow IT refers to using software, hardware, or IT services within an organization without the explicit approval of IT departments or management. Shadow IT often arises when employees use consumer-grade software or cloud services for business purposes or when teams within an organization build their tools or systems to support their work. It can pose a significant risk to businesses, resulting in data breaches, compliance violations, and other security incidents.
Q. How can Citizen Development help to mitigate the risks of Shadow IT?
Citizen Development, which involves non-technical employees creating their business applications, can help mitigate the risks of Shadow IT by bringing previously hidden IT projects and tools into the open, allowing IT departments to better understand and manage them. By providing employees with approved tools and platforms for building their own apps, businesses can promote innovation and collaboration while reducing the risks associated with Shadow IT.
Q. What are some common examples of Shadow IT, and how can they be identified?
Some common examples of Shadow IT include the use of consumer-grade cloud services, such as Dropbox or Google Drive, to store and share business data; the use of personal smartphones or tablets to access company data or systems; and the development of custom software or tools by teams within an organization without the approval of IT departments. Shadow IT can be identified through regular audits of software and hardware used by employees and through monitoring of network traffic and user behavior.
Q. What are the potential consequences of ignoring Shadow IT in terms of security and productivity?
Ignoring Shadow IT can have serious business consequences, including data breaches, regulatory violations, and productivity losses. Because Shadow IT is often developed and used without proper oversight or security measures, it can expose businesses to various security threats, from malware and ransomware to phishing attacks and data leaks. It can also result in inefficiencies and redundancies, as different teams within an organization may develop similar tools or systems independently, leading to a lack of standardization and control.
Q. How can organizations balance the benefits of Citizen Development with the need for robust security and governance?
Organizations can balance the benefits of Citizen Development with the need for robust security and governance by establishing clear policies and guidelines for Citizen Developers and providing training and support to help them understand the risks and responsibilities involved in building and using their own business applications.
IT departments can also provide approved platforms and tools for Citizen Developers to use, along with guidance on best practices for data privacy and security. Additionally, regular audits and monitoring can help ensure that all apps and systems used within an organization comply with established security and governance standards.
Login
Please login to comment
0 Comments
Oldest















